In my previous post, I was explaining how to deploy to Google Cloud. This guide explores leveraging GitHub Actions for continuous integration and deployment (CI/CD) of your Java applications to Google Cloud App Engine. I’ll focus on a secure approach using Workload Identity Federation, eliminating the need to store sensitive credentials in GitHub secrets.
Google Cloud Authentication
The question is how to authenticate from GitHub action to GCP. There are two ways 1) storing a long-lived JSON service account key in GitHub secrets or 2) Workload Identity Federation. I managed the first option in a few minutes but as I have to export a key and store it in GitHub this didn’t feel right. So I went for option two.
Luckily, there is documentation on GitHub that explains the process in detail, and I just had to adapt it.
Here’s a picture of how workflow identity federation works:
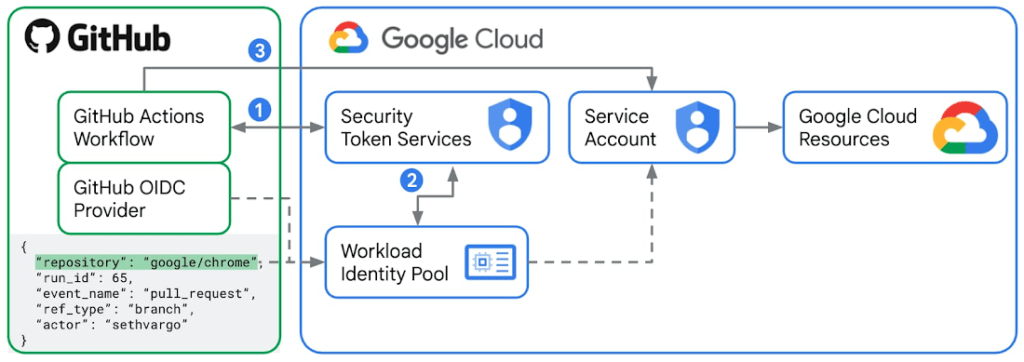
To make this work you have to:
– Create a Workload Identity Pool
– Add a Workload Identity Provider
– Allow authentications from the Workload Identity Provider to impersonate the Service Account
Simply follow the steps described in the instructions.
Once this is done you then can use the Workload Identity Pool and the Service Account in the GitHub action to authenticate before you deploy.
GitHub Action
Google Cloud provides google-github-actions and from these you can use the auth action:
- name: GCP Authentication
uses: google-github-actions/auth@v0
with:
workload_identity_provider: 'projects/839267018602/locations/global/workloadIdentityPools/playground-pool/providers/gha-provider'
service_account: 'github@organic-gecko-350604.iam.gserviceaccount.com'
In the next step deploy to App Engine. In my example the App Engine Maven plugin is used:
- name: Maven Build and AppEngine Deploy run: mvn -B package appengine:deploy -Pproduction
The source code is available here: https://github.com/simasch/vaadin-appengine-demo/
Conclusion
At first glance authentication with the JSON key may look simpler to configure. But once you have the Workload Identity Federation up and running there is no more need to add a secret on GitHub to store the key.
Ready to automate your App Engine deployments? Contact me for help.



